In an increasingly interconnected world, where every click and swipe opens a gateway to a universe of information, the need for robust cybersecurity measures has never been more crucial.
Cybercrimes are a regular concern for businesses, public entities, and individuals alike – you can easily become the prime target of a sophisticated cyberattack, ranging from email phishing to malware, and even ransomware.
Cyberattacks are an evolving threat that requires vigilant attention and a keen eye – let’s explore the various methods through which cyberattacks unfold, analyzing the inherent risks and uncovering the best strategies for you and your organization to confidently navigate the online sphere with confidence!
| What Is the Truth About Cyberattacks in 2023?
Cybercrime remains the foremost concern for businesses, with no individual, family, or company being immune to the risks posed by cyberattacks.
Cyberattacks have become increasingly sophisticated, emerging in various forms of malicious software – ransomware, phishing emails with embedded malware, and strategically deceptive social engineering schemes are just some of the tactics employed by cybercriminals. As these attacks continue to evolve, security systems face a persistent challenge in combating new and cunning strategies.
According to a 2023 Travelers Risk Index Case Study, 65% of participants perceived the business world as excessively risky due to daily cyber threats – protecting employee and customer data, securing company assets, and ensuring financial stability on top of maintaining seamless operations post-cyberattack was added stress for business owners, leading most to abandon the idea of pursuing their startup or attempting to rebuild their organization.
But that’s not all… The data on cyberattacks in 2023 showed the following:
- Security breaches surged by 27% for major organizations.
- Around 33% of backups fail following an attack.
- Data breaches have impacted approximately 47% of American adults.
- A significant 58% express daily concerns regarding cyber risks.
- Alarming figures indicate that 80% of small to medium-sized businesses have experienced the repercussions of cybercrimes, with many forced to shut down.
- Phishing remains the initial point of entry for 90% of cyberattacks.
And… 100% of digital users are prone to cyberattacks.
These statistics are disheartening for all – cyberattacks not only interrupt a company’s standing in the industry or jeopardize a family’s economic stability, but they also have far-reaching effects on the individuals connected to the affected organization or within the family network.
So… how can we begin to combat these threats?
| Identifying Cyberthreats
In 2021, the United States reached a new record for data breach incidents by officially exceeding 2,000 events, a 14% increase (all before the year had even concluded). According to PropertyCasualty360, phishing or other email scams were the main culprit of attacks, with the second most common attack being ransomware (with said attacks occuring every 11 seconds)!
All it takes is one simple misidentification or the opening of one unsuspecting email to trigger an attack, emphasizing the necessity for corporate entities to prioritize training in order to recognize and prevent malicious malware.
Here are a few ways you can identify malicious software or phishing attacks:
- Verify the sender: Malicious emails often impersonate trusted contacts, so always double-check the sender’s authenticity before opening any attachments. (Legitimate emails won’t come from a public email domain!)
- Beware of credential requests: Emails urging immediate profile updates, payments, or verification of suspicious activities can deceive recipients. Never click on email links demanding urgent action or threatening account deletion!
- Scrutinize the details: Is the email domain misspelt? Are there grammatical errors in the email? Does the affected link direct you to a suspicious site?
- Examine attachments: 37% of malicious emails contain .zip, .jar, or .exe attachments. Always ensure you can recognize links or files or verify sender addresses before opening any documents.
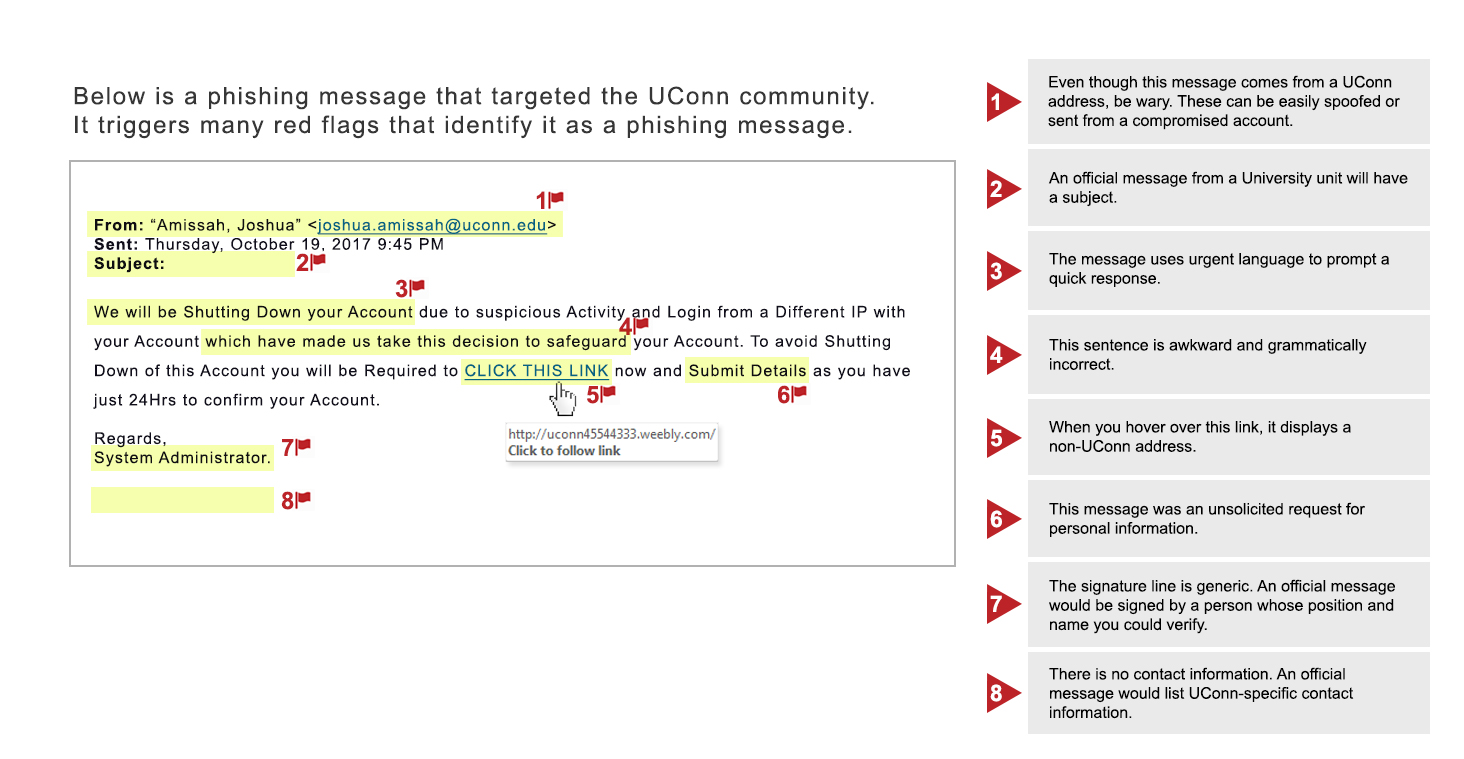
Image provided by UCONN IT Security
| How are Cyberattacks Combatted?
Combating cyberattacks requires a multifaceted strategy, necessitating proactive vigilance from everyone involved.
The collaborative efforts of all persons aim to drive improvements in cybersecurity and enhance the resilience of digital infrastructures against potential attacks. Here are some ways you can take control of you online information:
- Activate multifactor authentication: Ensure that all your logins involve a two-step verification process.
- Update software: Enable automatic updates to protect your devices from vulnerabilities.
- Use strong passwords: Create passwords that are at least 15 characters long, unique, and randomly generated.
- Stay updated with software: While human error often leads to network breaches, using the latest software can decrease the risk of an attack.
- Limit data transfers: Store sensitive data on personal devices to reduce the chance of exposure.
- Back up data: Safeguard critical data to minimize the impact of potential breaches or ransomware attacks.
- Regularly monitor for data leaks: Swiftly detect, respond to, and halt any suspicious activities with appropriate software.
- Develop a response plan: Establish a strategy to manage and contain potential or active breaches.
We are committed to promoting secure online practices and strengthening our digital defenses – let’s work together to establish a digital environment where safety and resilience serve as the foundation for innovation and secure data transmission!

Recent Comments